***Note***: These are my personal notes while studying for the CCNP Switch exam. Feel free to use them and by all means leave comments if you see any items that are incorrect or missing.
Chapter 1 – Campus Network Design
The Hierarchical Design Model
3 level design model – Access, Distribution and Core layers
- Access layer – end-user access, computers, phones, wireless access points. HA offered through redundant power, and first hop redundancy protocols. QoS and multicast support. Layer 2 security via DAI, DHCP snooping, BPDU Guard, port-security, IP source-guard.
- Distribution layer – Aggregation of access switches. HA through redundant connections to access layer switches and to core. Layer 3 boundary where routing meets the access layer vlans. Can be default gateway for access devices. QoS and security applied. Segmentation of workgroups and network problems from the core. Combination of L2 and L3 switching.
- Core layer – High speed L3 pathing. HA through redundant components. No policies such as ACL’s or filters to slow traffic.
Design layers in “blocks” – a group of access layer switches and their distribution switches. Collapsed core/distribution layer in smaller campus designs (less than 200 end devices).
Switch blocks and proper vlan planning prevent issues such as broadcasts from being propagated out to the core and other switch blocks. VLANs should not extend beyond distribution switches.
Network design planning – PPDIOO
- Prepare – Organizational requirements gathering, high level architecture, network strategy, business case strategy.
- Plan – Network requirements gathering, network examination, gap analysis, project plan.
- Design – Comprehensive, detailed design.
- Implement – Detailed implementation plan, and implementation following its steps.
- Operate – Day to day network operation and monitoring.
- Optimize – Proactive network management and fault correction.
Chapter 2 – VLANs
VLANs – logically group users, departments, etc. Segment broadcast domains. Subnet correlation. Access control. Quality of service.
End to end vlans – vlans extend across the campus. User vlan membership follows them across the network.
Local vlans – do not extend past the distribution layer. Inter-vlan traffic routed. Created around physical boundaries.
Trunking
Trunking, or vlan tagging, passes multi-vlan information across inter-switch links. Switches will strip the vlan tag before sending traffic to an access port. Trunk ports leave these tags intact.
There are two types of tagging – ISL and 802.1Q
ISL – Inter Switch Link. Cisco proprietary. Deprecated. Encapsulates the original frame with an ISL header, recalculates the CRC.
802.1Q – Open/Industry standard. Inserts tag into the frame rather than encapsulating. Inserts a 4 byte “shim” into the frame after the source and destination MAC and before the data.
Native Vlan – If trunk ports receive an untagged packet they will assign the native vlan to that packet. Best practice to assign native vlan to an unused vlan.
- switchport trunk native vlan xxx
Dynamic Trunking Protocol (DTP)
Switches can/will auto negotiate trunks using DTP.
Several modes: Access (never a trunk), Trunk (always a trunk), Dynamic Auto (will listen for but not request trunking), Dynamic Desirable (will listen to and actively request trunking), Nonegotiate (ignores all DTP).
Switches out of the box are set to Dynamic Desirable – ports will auto negotiate trunks. This is a security risk. Disable with nonegotiate. (Do not use DTP).
Helpful commands:
- show interface fa0/1 switchport
- show interface fa0/1 trunk
VLAN Planning
IP addressing scheme (numbering, naming), VLAN placement (local or end-to-end), Trunks?, VTP?, Test and Verification.
VTP – Vlan Trunking Protocol
A vlan replication method, uses revision numbers to propagate vlan info across switches.
vlan.dat file in old switches can cause issues
3 modes:
- Server (default) – power to change vlan information, sends and receives vlan updates, saves vlan configuration in nvram
- Client – cannot change vlan information, sends and recieves vlan updates, does not save vlan configuration in nvram
- Transparent – power to change vlan information, forwards updates (pass-through), does not listen to VTP advertisements, saves vlan configuration in nvram
Helpful commands:
- vtp domain cisco
- vtp mode
- vtp password supersecret
- vtp version <1|2>
- show vtp status
- show vtp counters
VTP pruning – Because switches will forward broadcast traffic out all ports, including trunk ports (if that vlan exists across the trunk) broadcast traffic can potentially be sent out to every switch in a network. VTP pruning helps reduce unnecessary flooded traffic by pruning traffic from vlans that do not exist on the adjoining switch(es). If the switch on the receiving end of the trunk does not have ports in that VLAN, the vlan is pruned.
Enabled on a VTP server: vtp pruning
Chapter 3 – Spanning Tree Protocol
STP – 802.1D
RSTP – 802.1w
MST – 802.1s
Original STP was created to prevent loops. Switches send probes (Bridge Protocol Data Units – BPDU’s) into the network to discover loops. BPDU’s help elect the core switch or root bridge.
Essentially: All switches determine the best way to reach the root bridge and then block all other redundant links.
BPDU’s are sent every 2 seconds. Each switch has a unique Bridge ID – an 8 byte value consisting of a 2 byte Bridge Priority value between 0 and 65535 – the default is 32768, and the 6 byte MAC address. LOWER IS BETTER!
Three port types:
- Root Port – used to reach the root bridge
- Designated port – forwarding port, one per each network segment
- Blocking/Non-designated port
The Root Bridge is the bridge with the lowest Bridge ID (Bridge Priority + MAC Address).
The Root Ports are elected by using the root path cost of all of the cumulative links leading to the root bridge. Path costs are determined by the link bandwidth:
- 4Mbps – 250
- 10Mbps – 100
- 16Mbps – 62
- 45Mbps – 39
- 100Mbps – 18
- 155Mbps – 14
- 622Mbps – 6
- 1Gbps – 4
- 10Gbps – 2
Designated Ports are elected by the lowest path cost to the root. Tie breakers are:
- Lowest root bridge ID
- Lowest root path cost to the root bridge
- Lowest sender bridge ID
- Lowest sender port ID
Switch ports progress through several states when participating in STP:
- Disabled – does not send/receive any data
- Blocking – will receive BPDUs, does not learn MAC addresses, does not send/receive data
- Listening – sends/receives BPDUs, does not learn MAC address, does not send/receive data
- Learning – sends/receives BPDUs, learns MAC addresses, does not send/receive data
- Forwarding – sends/receives BPDUs, learns MAC addresses, sends/receives data
Helpful commands:
- show spanning-tree interface
- debug spanning-tree switch state
Manual STP Computations – to work out a spanning-tree topology using a network diagram:
- Identify path costs on links
- Identify the root bridge
- Select root ports (1 per switch)
- Select designation ports (1 per segment)
- Identify blocking ports
STP Timers – STP uses three timers to make sure that the network converges properly before a loop can occur.
- Hello Time – Default value is 2 seconds. The time between configuration BPDUs sent by the root bridge. The Hello Time for all nonroot switches is determined by the root switch. Locally configured Hello Times are used to send TCN BPDUs.
- Forward Delay – Default value is 15 seconds. The time interval that a switch port spends in both the Listening and Learning states.
- Max Age – Default value is 20 seconds. The time interval that a switch stores a BPDU before discarding it.
A topology change notification (TCN) BPDU is sent out on a switches root port when any port comes up or goes down. The sending switch continues to send TCN BPDUs every Hello Timer interval until it gets an acknowledgement from its upstream neighbour. Upstream switches propagate it onward toward the root bridge and send their own acknowledgement. When the root bride receives the TCN BPDU it sets the Topology Change flag in its Configuration BPDU which is sent out to every other bridge in the network. This causes all other bridges to shorten their bridge table aging times to the Forward Delay value (15 seconds) from the default 300 seconds. This flushes all learned MAC addresses other than devices communicating during the change. This condition lasts for the sum of the Forward Delay and the Max Age timers (default of 15 + 20 seconds = 35 seconds).
- Per-VLAN Spanning Tree (PVST): Cisco proprietary, operates a separate instance of STP for each VLAN. Requires ISL trunks and is therefore incompatible with CST (Common Spanning-Tree)
- Per-VLAN Spanning Tree Plus (PVST+): Cisco proprietary but allows interoperation with CST. Operates over 802.1Q and ISL trunks.
Commands for configuring and tuning STP:
- spanning-tree vlan 5 priority 4096
- spanning-tree vlan 5 root primary|secondary
- show spanning-tree interface Gi0/1 [cost]
- spanning-tree vlan 5 cost 2
- spanning-tree vlan 5 hello-time {seconds}
- spanning-tree vlan 5 forward-time {seconds}
- spanning-tree vlan 5 max-age {seconds}
- show spanning-tree
- show spanning-tree detail
- show-spanning tree vlan 5
- show spanning-tree vlan 5 summary
- show spanning-tree vlan 5 root
- show spanning-tree vlan 5 bridge
Redundant Link Convergence (Cisco Proprietary):
- PortFast – Enables fast connectivity to the access-layer ports
- spanning-tree portfast
- UplinkFast – Enables fast-uplink failover on access layer switches when dual uplinks are connected to the distribution layer
- spanning-tree uplinkfast
- BackboneFast – Enables fast convergence in the core layer switches after a spanning-tree topology change
- spanning-tree backbonefast
Protecting Spanning-Tree:
- Root Guard – prevents a downstream switch from sending BPDU’s. Used on ports where you would never expect to see the root bridge. Port is placed in a root-inconsistent state if a BPDU is received. Once BPDU’s stop, the port transitions through the normal STP stages.
- spanning-tree guard root
- BPDU Guard – Protects a PortFast port against receiving BPDU’s. Immediately puts the port into errdisable state.
- Globally enable on all portfast ports: spanning-tree portfast bpduguard default
- Enabled on a per-port basis: spanning-tree bpduguard enable
- Loop Guard – Keeps track of BPDU activity on nondesignated ports. If BPDU’s go missing, Loop Guard moves the port into a loop-inconsistent state. The port effectively blocks to prevent a loop from forming. Blocks on a per-vlan basis, not the entire port.
- Globally enabled on all ports: spanning-tree loopguard default
- Enabled on a per-port basis: spanning-tree guard loop
- UDLD – Protects bidirectional links from becoming unidirectional. This is typically only on fibre connections. Potential for BPDU’s to not be received on one side of the link. Special layer 2 frames are sent and the far end switch echoes those frames back across the same link. Prevents STP from moving a blocked port to the forwarding state.
- Normal mode: port is allowed to continue operation, marks the port as undetermined and generates a syslog message.
- Aggressive mode (recommended): UDLD messages are sent out once a second for 8 seconds, if none are echoed back the port is errdisabled.
- Globally enabled for all fibre-optic ports: udld {enable|aggressive}
- Enabled on a per-port basis: udld {enable|aggressive}
- Must be enabled on both sides of a link
- BPDU Filtering – Prevents BPDU’s from being sent or processed on a switch port, effectively disabling STP on that port.
- Globally enabled on all portfast ports: spanning-tree portfast bpdufilter default
- Enabled on a per-port basis: spanning-tree bpdufilter {enable|disable}
Helpful Commands:
- show spanning-tree inconsistentports
- show spanning-tree interface Gi0/1 [detail]
- show spanning-tree summary
- show udld
- udld reset
Note to self: Root guard is always going to be on a designated port, facing AWAY from the root bridge. Loop guard is always going to be on a blocking port on the other side from a designated port, facing TOWARDS the root bridge.
Advanced Spanning Tree Protocol
Original STP – 802.11D – topology changes can cause 30 seconds or more of interruption. 802.1w – Rapid Spanning Tree – was developed to use the same principal concepts but make convergence time much faster.
RSTP can be a single instance or multiple instances (Rapid PVST+). RSTP is also part of IEEE 802.1s (Multiple Spanning Tree, MST).
Root bridge election happens the same way with RSTP. The following port roles are determined:
- Root port – identical to 802.1D
- Designated port – one per segment
- Alternate port – alternate path to the root (alternate root port)
- Backup port – redundant but less desirable path to another switch (alternate designated port)
RSTP port states:
- Discarding – frames are dropped, no MAC addresses are learned
- Learning – frames are dropped, MAC addresses are learned
- Forwarding – normal port operation
In 802.1D BPDU’s are sent out from the root bridge. In RSTP BPDU’s are sent out every switch port at Hello Time intervals, any switch anywhere in the network plays a role in the topology. If 3 BPDUs are missed, that neighbor is presumed down and related data is aged out. This takes only 6 seconds versus the Max Age timer in 802.1D (20 seconds). RSTP distinguishes its BPDUs from 802.1D so it can coexists with switches running STP.
RSTP Convergence:
- One common root bridge is selected
- The state of every switch port is brought from Blocking to an appropriate state to prevent loops
RSTP forwarding decisions are based on the type of port:
- Edge port – port connected to a single host (PortFast), is immediately put in a forwarding state
- Root port – best path cost to the root
- Point-to-point port – any port that connects to another switch and becomes a designated port. Decided by an exchange of BPDUs (handshake).
Non-edge ports begin in the discarding state. BPDUs are exchanged and the Root Bridge is identified. If a port receives a superior BPDU from a neighbor that port becomes the root port. For each non-edge port the switch exchanges a proposal-agreement handshake to determine the state of each end of the link.
- If the proposal’s sender has a superior BPDU – the switch realizes the sender should be the designated switch and it’s own port must become the new root port.
- Before the switch agrees to anything it must synchronize to the topology
- All non-edge ports immediate are moved into the Discarding state so no bridging loops can occur
- An agreement message is sent back to the sender indicating that the switch is in agreement with the new designated port choice. This also tells the sender that the switch is in the process of synchronizing itself
- The root port immediately moves to Forwarding, the sender’s port can also begin Forwarding
- For each non-edge port that is Discarding, a proposal message is sent to the respective neighbor.
- An agreement is expected and received
- The non-edge port immediately moves to the Forwarding state
RSTP convergence can be seen as a cascading process outward from the root bridge towards the outer edges of the network. If a designated port sends a proposal and no agreement is received the sending switch then resorts to 802.1D rules and transitions through the legacy port states before moving to the Forwarding state.
RSTP detects a topology change only when a non-edge port transitions to the Forwarding state. BPDU’s with their Topology Change (TC) bit set are sent out all non-edge designated ports. This is done until the TC timer expires (2 x Hello Time – 4s). All MAC addresses for non-edge designated ports are flushed from the CAM table. All neighboring switches that receive the TC messages also flush MAC addresses learned on all ports except the one that received the TC message. Those switches then send TC messages out non-edge designated ports, and so on.
RSTP Configuration
By default a switch operates in PVST+ mode using traditional 802.1D STP. The switch must be configured to use RPVST+ or MST to use RSTP – as it is simply the underlying mechanism that a spanning-tree mode uses to detect topology changes.
- To configure an RSTP port as an edge port, enable portfast.
- spanning-tree portfast
- RSTP decides a port is a point-to-point link by default if operating in full duplex mode.
- spanning-tree link-type point-to-point
Rapid Per-VLAN Spanning Tree Protocol
To change the STP mode and begin using RPVST+ the following global command is used:
- spanning-tree mode rapid-pvst
Multiple Spanning Tree Protocol
MST allows mapping one or more VLANs to a single STP instance. MST is configured in “Regions” – within which all switches must run the instance of MST that is configured with:
- MST configuration name (32 characters)
- MST configuration revision number (0 to 65535)
- MST instance-to-VLAN mapping table (4096 characters)
Within a single MST region, n Internal Spanning tree instance runs to work out a loop-free topology between links where CST meets the region boundary and all switches inside the region. The IST presents the region as a single virtual bridge to the CST outside. BPDUs are exchanged only at the region boundary over the native VLAN of trunks, as if a signle CST were in operation.
Inside a region, the actual MST instances (MSTI) exist alongside the IST. The IST always exists as MSTI number 0 leaving MSTI 1 through 15 available for use.
MST Configuration
- Enable MST on the switch
- spanning-tree mode mst
- Enter MST configuration mode
- spanning-tree mst configuration
- Assign a region configuration name
- name {name}
- Assign a region configuration revision number
- revision {version}
- Map VLANs to an MST instance
- instance {instance-ID} vlan {vlan-list}
- Show pending changes
- show pending
- Exit the MSt configuration mode to commit changes to the active MST region configuration
- exit
The switch stops PVST+ operation and begins RSTP operation.
Summary
- STP – Spanning Tree Protocol
- 802.1D – Common Spanning Tree (CST) – single instance of STP for all VLANs
- PVST+ – One instance of STP is used for each active VLAN
- RSTP – Rapid Spanning Tree Protocol
- RPVST+ – One instance of RSTP is used for each active VLAN
- MST – Allows multiple VLANs to be mapped to a single RSTP instance
Chapter 4 – Multilayer Switching
Inter VLAN Routing
Vlans are Layer 2 broadcast domains and traffic does not pass from one VLAN to another. A Layer 3 device is needed to transport packets between VLANs. This is accomplished through one of several methods:
- A router connected to each VLAN on a switch with a physical link
- A router connected to a switch with a trunk and virtual interfaces on a single physical interface (AKA Router on a stick)
- A multilayer switch
Multilayer switches can perform Layer 2 switching and interVLAN routing. Layer 3 addresses can be assigned to a physical interface or to a virtual interface on a multilayer switch.
Configuring a switchport between L2 and L3 modes: switchport or no switchport
IP Routing must be enabled for interVLAN routing: ip routing
Port Configurations:
- Switchport – Layer 2
- interface gi1/0/1
- switchport
- Routed – Layer 3
- interface gi1/0/1
- no switchport
- ip address x.x.x.x x.x.x.x
- Switch Virtual Interface (SVI) – Layer 3
- interface vlan xxx
- ip address x.x.x.x x.x.x.x
- no shutdown
- The VLAN (layer 2) must be defined on the switch in order for the SVI to be used.
Multilayer Switching with CEF
Catalyst switches can forward packets based on Layer 3 and Layer 4 information. Catalyst multilayer switches use Cisco Express Forwarding (CEF). In traditional MLS, the route processor (RP) receives the first packet of a new flow, and routes that packet as usual. The switching engine (SE) listens to that first packet, and then learns the path for subsequent packets to be switched directly to the destination without using the RP. This is also known as Netflow Switching or Route Cache Switching.
CEF offers high performance packet forwarding in hardware, vs. traditional routing which occurs in software.
The Layer 3 Engine maintains routing information in an ordered list from most specific to least specific – this is called the Forwarding Information Base. The FIB contains the next hop for each entry. Any changes to the routing table causes an update to the FIB as well.
To view the FIB table: show ip cef
Some packets cannot be switched in hardware. These are punted to the Layer 3 engine for normal software processing:
- Entries not located in the FIB
- FIB table is full
- TTL expired
- MTU exceeded – packet must be fragmented
- ICMP redirect
- Unsupported encapsulation type
- Tunneled packets
- An access list with the log option is triggered
- NAT (Cat6500 with Sup720 can do NAT in hardware)
Normal Router: Routing Table (next hop info) + ARP Table (MAC to IP information)
Multilayer Switch: FIB Table (next hop info) + Adjacency Table (MAC adjacencies)
The FIB also has corresponding Layer 2 information for every next-hop entry in the Adjacency Table.
Helpful Commands:
- show adjacency
- show adjacency summary
- show adjacency detail
As a next-hop address receives a valid ARP entry the adjacency table is updated. If an ARP entry does not exist the entry is marked as “CEF glean” in the FIB and packets are sent to the Layer 3 engine for processing.
If valid entries exist in the FIB and adjacency table, the packet header is then rewritten the same way it would be on a traditional router, but in dedicated packet-rewrite hardware:
- Layer 2 source and destination address changes
- Layer 3 TTL decremented by one
- Layer 3 checksum
- Layer 2 frame checksum
CEF is enabled by default on all CEF-capable switches but can be disabled with the no ip route-cache cef and no ip cef commands.
DHCP on a Multilayer Switch
DCHP defined by RFC 2131 – uses a client/server model. Hosts requesting IP addresses use a client, and the address assignment is handled by a server. DHCP negotiation happens in four steps:
- The client sends a DHCP Discover message as a broadcast
- A DHCP server replies with a DHCP Offer message (broadcast)
- The client sends a DHCP Request message (broadcast)
- The DHCP server replies with a DHCP ACK message (broadcast)
Because DHCP relies on broadcasts, hosts in the same VLAN are able to request addresses. One DHCP server per VLAN might be required but this can be worked around using DHCP Relay.
Configuring an IOS DHCP Server:
- ip dhcp excluded-address {start ip} {end ip}
- ip dhcp pool {pool-name}
- network {ip address} {subnet mask}
- default-router {ip address}
- lease {infinite|dd hh mm}
- exit
Configuring a DHCP Relay
If a DHCP server is centrally located, you can relay DHCP requests between clients and servers, even on different VLANs or subnets. Configuring a layer 3 interface that will be used as the default gateway for clients – this will act as the DHCP relay. Then use the ip helper-address command to identify the location of the DHCP server.
Chapter 5 – Layer 3 High Availability
Router Redundancy in Multilayer Switching
Just as with routers, multilayer switches should provide a means of preventing a VLAN from becoming isolated. They can provide the same layer 3 redundancy mechanisms as a router such as:
- Hot Standby Router Protocol (HSRP)
- Virtual Router Redundancy Protocol (VRRP)
- Gateway Load Balancing Protocol (GLBP)
These are also called first-hop redundancy protocols (FHRP).
Hot Standby Router Protocol – HSRP
Cisco proprietary, allows several routers or multilayers switches to appear as a single gateway IP address. RFC 2281.
One router becomes active, another standby, and the rest ‘listen’. Hello messages are exchanged at regular intervals. HSRP sends messages to the multicast address 224.0.0.2 (“all routers”) on UDP port 1985. HSRP groups can be assigned an arbitrary number from 0 to 255 but most switches only support up to 16 HSRP groups. HSRP group numbers are locally significant to an interface so you can have HSRP group 1 on interface VLAN 10 as well as HSRP group 1 on interface VLAN 11.
HSRP Election:
- Priority value: 0-255, 100 is default. Highest wins.
- Ties broken by highest IP address on the HSRP interface.
HSRP Configuration:
- standby 1 priority 200
HSRP States:
- Disabled
- Init
- Listen
- Speak
- Standby
- Active
*Only the standby router monitors hello messages from the active router. Hellos are sent every 3 seconds by default. If Hellos are missed for the duration of the hold time timer (default is 10 seconds, or 3 x the Hello Timer) the standby router is clear to assume the active role.
At that time other routers in the Listen state will elect a new Standby router based on priority values or IP address.
Changing timer values:
- standby {group} timers [msec] hello [msec] holdtime
- Holdtime should always be at least 3x the Hello Time
A failed active router will not immediately become active again if it is restored, even with a higher priority value. Preemption must be enabled for this to happen.
- standby 1 preempt [delay [min seconds] [reload seconds]]
Minimum forces the router to wait for x seconds before attempting to preempt the active router.
Reload forces the router to wait for x seconds after it has been reloaded or restarted before preemption. This allows time for routing protocol convergence.
HSRP can use plaintext or MD5 authentication to prevent unauthorized routers from participating in HSRP.
- standby 1 authentication [string]
- standby 1 authentication md5 key-string [0 | 7] [string]
- MD5 key strings can also be a key on a key chain
HSRP can track a specific interface and then reduce a routers’ priority if that interface goes down, or increment it when it comes back up.
- standby 1 track [interface] [decrement value]
Note that in order for another router to become active in this scenario, it must have a higher HSRP priority value and must have preemption enabled.
*Without preemption the active role cannot be given to any other router.
HSRP MAC address: 0000.0c07.acxx where xx is the 2-digit hex HSRP group number
HSRP Configuration Example:
- interface vlan 50
- ip address 192.168.1.10 255.255.255.0
- standby 1 priority 200
- standby 1 preempt
- standby 1 ip 192.168.1.1
Virtual Router Redundancy Protocol – VRRP
- Standards based alternative to HSRP
- RFC 2338
- Master router, backups
- Group numbers: 0 to 255
- Priority values: 1 to 254 (100 is default)
- MAC address: 0000.5e00.01xx (where xx is a two-digit hex VRRP group number)
- Advertisements sent every 1 second, backup routers can learn advertisement interval from the master
- By default backup routers are configured to preempt
- Multicast advertisements to 224.0.0.18 using IP port 112
VRRP Configuration:
- vrrp 1 priority 200
- vrrp 1 timers advertise [msec] interval
- vrrp 1 timers learn
- no vrrp 1 preempt
- vrrp 1 preempt [delay seconds]
- vrrp 1 authentication string
- vrrp 1 ip xxx.xxx.xxx.xxx [secondary]
- vrrp 1 track object [decrement priority]
VRRP Verification:
- show vrrp
- show vrrp brief
Gateway Load Balancing Protocol – GLBP
Cisco proprietary protocol that allows multiple switches (or routers) to participate in forwarding and load-balancing traffic. Clients still use the same default gateway virtual IP address, and load balancing is done through the use of virtual MAC addresses in ARP replies returned to the clients.
- One router is elected the active virtual gateway (AVG)
- The AVG answers all ARP requests for the virtual router address, and replies based on the load-balancing algorithm used
- AVG assigns virtual MAC addresses to the other routers participating in the group, referred to as active virtual forwarders (AVF)
- Other routers in the group serve as backups or secondary virtual forwarders in case the AVF fails
- The AVG also assigns backup roles
GLBP Configuration:
- glbp group priority level
- GLBP group ranges from 0 to 1023
- Router priority ranges from 1 to 255, default is 100 with 255 the highest
- glbp group preempt [delay minimum seconds]
The AVG sends hello messages (default 3 seconds) as do GLBP peers. If hellos are not received within the holdtime (default 10 seconds) that peer is presumed to have failed. Configure the timers on the AVG, these are advertised and all peers will learn those values.
- glbp group timers [msec] hellotime [msec] holdtime
AVF’s are assigned a virtual MAC address: 0007.b4xx.xxyy where xx.xx is a 16 bit value: 6 zero bits followed by the 10 bit GLBP group number. The yy value us the 8 bit virtual forwarder number.
GLBP Load Balancing
- Round Robin – Each virtual MAC address is used in order, traffic is evenly distributed across all AVFs. Default.
- Weighted – GLBO group interface’s weighting determines the proportion of traffic that is sent to that AVF.
- Host dependent – Each client always receives the same AVF reply.
- glbp group load-balancing [round-robin | weighted | host-dependent]
Enabling and verifying GLBP
- glbp group ip [ip-address [secondary]]
- show glbp
- show glbp brief
Supervisor and Route Processor Redundancy
Modular switch platforms can accept two supervisor modules in a single chassis. The second supervisor is redundant and will take over in the event the first supervisor fails. These can be configured in several modes:
- Route Processor Redundancy (RPR) – The redundant supervisor is only partially booted and the supervisor and route engine initialized. During a failure the standby module must reload every other module in the switch and then initialize all supervisor functions.
- Route Processor Redundancy Plus (RPR+) – The redundant supervisor is booted and initialized. No L2 or L3 functions are started. During a failure the standby module completes initialization without reloading the other modules. Switch ports retain their state.
- Stateful Switchover (SSO) – The redundant supervisor is fully booted and initialized. Both startup and running configs are synchronized. L2 information is maintained on both supervisors. Switch interface state maintained on both supervisors, no link flap during a failover.
Nonstop Forwarding
NSF (Cisco proprietary) is another feature available that helps rebuild the Routing Information Base (RIB) quickly with assistance from other NSF-aware neighbours. The RIB is used to generate the FIB for CEF.
Chapter 6 – Campus Network Security
Port Security
- Controls what can be connected to a switch using MAC addresses
- 1 MAC address by default – can be 1 to 1024
- Learned or “sticky” MAC addresses
- Violations can:
- Protect – Port stays up, packets from violating MAC are dropped, no record of the violation is kept
- Restrict – Port stays up, packets from violating MAC are dropped, switch keeps count of violating packets and can send an SNMP trap and Syslog message as an alert
- Shutdown – Port is immediately err-disabled., and must be re-enabled manually or through err-disable recovery
Port Security Configuration:
- switchport port-security
- switchport port-security maximum max-addr
- switchport port-security mac-address mac-addr
- switchport port-security violation {shutdown | restrict | protect}
Port-Based Authentication
- 802.1x
- Combination of AAA authentication and port-security
- EAPOL (Extensible Authentication Protocol Over LAN) is a L2 protocol
- Port remains in an unauthorized state, client computer must be 802.1x-capable
802.1x Configuration:
- aaa new-model
- radius-server host {hostname | ip-address} [key string]
- aaa authentication dot1x default group radius
- dot1x system-auth-control
- interface interface
- dot1x port-control {force-authorized | force-unauthorized | auto}
- force-authorized – the port is forced to always authorize any connected client – default state
- force-unauthorized – the port is forced to never authorize any connected client
- auto – the port uses an 802.1x exchange to move from unauthorized to authorized, requires an 802.1x capable client
- dot1x host-mode multi-host (if multiple hosts are expected on the port)
Mitigating Spoofing Attacks
DHCP Snooping:
- Helps prevent rogue DHCP servers
- Switch intercepts broadcast DHCP messages before sending them out to the rest of the VLAN
- Legitimate DHCP servers are identified on trusted ports
- DHCP replies from an untrusted port are discarded
- Also keeps track of DHCP bindings for legitimate replies
- Configured on a per-VLAN basis
DHCP Snooping Configuration:
- ip dhcp snooping
- ip dhcp snooping vlan 104
- interface range fastethernet 0/21 – 22
- ip dhcp snooping limit rate 3
- interface gigabitethernet 0/1
- ip dhcp snooping trust
IP Source Guard
- Mitigates address spoofing
- Uses DHCP Snooping database and static IP source binding entries
- Switch learns the MAC and IP address of hosts that use DHCP
- Packets arriving on a switch port must match source IP learned by DHCP Snooping or a static entry
- Packets arriving on a switch port must match source MAC address learned on a switch port and by DHCP Snooping
- Non-matching packets are dropped
- DHCP Snooping must be enabled
- To detect spoofed MAC addresses, port security is also required
IP Source Guard Configuration:
- interface interface
- ip verify source [port-security]
Dynamic ARP Inspection
- Mitigates ARP poisoning or spoofing (man in the middle)
- Similar to DHCP Snooping, ports are trusted or untrusted
- ARP packets are intercepted on untrusted ports, nothing is done on trusted ports
- The switch verifies the MAC and IP against known trusted values (static entries or DHCP Snooping database)
DAI Configuration:
- ip arp inspection vlan 104
- arp access-list StaticARP
- permit ip host 192.168.1.10 mac host 0006.5b02.a841
- exit
- ip arp inspection filter StaticARP vlan 104
- interface gigabitethernet 0/1
- ip arp inspection trust
- show ip arp inspection
Best Practices for Securing Switches
- Configure secure passwords
- Use system banners
- Secure the web interface
- Secure the switch console
- Secure virtual terminal access
- Use SSH whenever possible
- Secure SNMP access
- Secure unused switch ports
- Secure STP operation
- Secure the use of CDP
VLAN Security
VLAN Access Lists
- VACLs are configured as a VLAN access map (similar to a route map)
- VACLs permit, deny or redirect packets within a VLAN
- Create the access-map, define statements and actions (drop, forward, capture, redirect)
- Apply the VACL to a VLAN (not a VLAN SVI)
- TCAM performs the VACL match and action
VACL Configuration – host 192.168.99.17 is not allowed to contact any other host on it’s local subnet
- ip access-list extended local-17
- permit ip host 192.168.99.17 192.168.99.0 0.0.0.255
- exit
- vlan access-map block-17 10
- match ip address local-17
- action drop
- vlan access-map block-17 20
- action forward
- exit
- vlan filter block-17 vlan-list 99
Private VLANs
- Restricts traffic within a VLAN
- Ex: Server farm – servers all need to talk to the gateway/router but do not need to receive each others’ broadcasts
- Service Provider example to segregate clients on a single VLAN
- Primary VLANs associated with secondary VLANs
- Host associated with a secondary VLAN can communicate with the primary VLAN but not with another secondary VLAN
- Secondary VLANs are either:
- Isolated – Can reach the primary VLAN but not any other secondary VLAN or other isolated hosts
- Community – Can communicate with the primary VLAN and each other, but not any other secondary VLAN
- Only locally significant, VTP does not pass information about private VLANs
- Each port using a private VLAN must use one of the following modes:
- Promiscuous – The port can communicate with anything else connected to the primary or any secondary VLAN.
- Host – The port connects to a host that resides on an isolated or community VLAN. The port only communicates with an promiscuous port or ports on the same community VLAN
Private VLAN Configuration:
- vlan 10
- private-vlan community
- vlan 20
- private-vlan community
- vlan 30
- private-vlan isolated
- vlan 100
- private-vlan primary
- private-vlan association 10,20,30
- exit
- interface range fastethernet 1/1 – 1/2
- switchport mode private-vlan host
- switchport private-vlan host-association 100 10
- exit
- interface range fastethernet 1/4 – 1/5
- switchport mode private-vlan host
- switchport private-vlan host-association 100 20
- exit
- interface fastethernet 1/3
- switchport mode private-vlan host
- switchport private-vlan host-association 100 30
- exit
- interface fastethernet 2/1
- switchport mode private-vlan promiscuous
- switchport private-vlan mapping 100 10,20,30
Securing VLAN Trunks
Switch spoofing
- DTP is a security risk
- To prevent switch spoofing use nonegotiate or manually configure trunk links to prevent auto-negotiation
VLAN Hopping
- Double-tagged frames can traverse VLAN boundaries
- Revolves around the use of untagged native VLAN
- Set the native VLAN of a trunk to a bogus or unused VLAN
- Prune the native VLAN off both ends of the trunk
- vlan 800
- name bogus_native
- exit
- interface gigabitethernet 1/1
- switchport trunk encapsulation dot1q
- switchport trunk native vlan 800
- switchport trunk allowed vlan remove 800
- switchport mode trunk
Alternatively, force all 801.Q trunks to add tags for the native VLAN:
- vlan dot1q tag native
Chapter 7 – Campus Network Services
IP Telephony
Power Over Ethernet (PoE)
- Cisco Inline Power (ILP) – developed before the IEEE 802.3af standard
- IEEE 802.3af – standards-based PoE that offers vendor interoperability
- Power classes:
- (Default) Class 0 – 15.4W
- Class 1 – 4.0W
- Class 2 – 7.0W
- Class 3 – 15.4W
- Class 4 – Up to 50W (PoE+)
- For Cisco ILP power is provided over data pairs 2 and 3 (pins 1,2 and 3,6)
- For IEEE 802.3af power can be supplied on the same pairs, or over pairs 1 and 4 (pins 4,5 and 7,8)
- Configured with: power inline {auto | static | never}
- Verified with: show power inline
Voice VLANs
- Cisco IP phones provide a data connection for a user’s PC as well as it’s own voice stream
- Allows one Ethernet drop per user
- Switch ports can only be access (single vlan) or trunk (multiple vlan)
- Voice vlans allow a special case voice vlan to be added on a single-vlan access port
- Configured with: switchport voice vlan {vlan-id | dot1p | untagged | none}
- Voice and user data carried over separate VLANs
- VoIP packets in the voice VLAN carry CoS bits in the 802.1p trunk encapsulation field
- Automatically enabled through CDP
Voice QoS
- Voice traffic is subject to delay, jitter and loss
- QoS can be implemented to address these conditions
- Three basic types:
- Best-effort delivery
- Integrated services model
- Differentiated services model
Best Effort Delivery – packets forwarded in the order they were received, regardless of type or need for priority
Integrated Services Model – IntServ prearranges a path for priority data. Beginning with RFC 1633 Resource Reservation Protocol (RSVP) was developed to schedule and reserve adequate path bandwidth. The source application requests QoS through RSVP, and each network device along the path must check to see if it can support the request. Does not scale well.
Differentiated Services Model – DiffServ allows each device on the network to make it’s own forwarding decisions based on QoS policy. DiffServ bases QoS decisions on information in each packet header.
DiffServ QoS
- DiffServ is per-hop behaviour, each router or switch inspects the packet header to determine how to forward the packet
Layer 2 Classification
- Layer 2 frames have no mechanism to indicate priority
- A switch can only forward frames based on best-effort delivery
- When frames travel from switch to switch, they are encapsulated and class of service (CoS) can be assigned
- IEEE 802.1Q – Frames are tagged with a 12 bit VLAN ID and a User field. The User field contains three 802.1p priority bits that indicate CoS. This ranges from 0 to 7 (lowest to highest priority). Frames on the native VLAN are not tagged, and receive default CoS.
- ISL – Frames are tagged with a 15-bit VLAN ID. Next to the frame Type field is a 4-bit User field. The lower 3 bits are marked as a CoS value.
Layer 3 QoS Classification with DSCP
- Packets have always had a type of service (ToS) byte – 3-bit IP Precedence value, and 4-bit ToS value
- 3 bits of IP Precedence used to describe per-hop QoS behaviour
- DiffServ uses this ToS byte as a Differentiated Services (DS) field
- 6-bit DS value is called the Differentiated Services Code Point (DSCP)
- Divided into a 3-bit Class Selector and a 3-bit Drop Precedence value

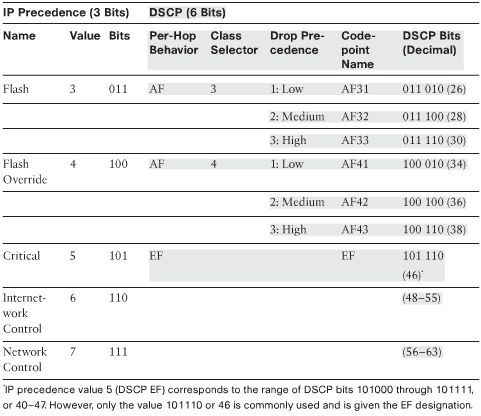
- Mapping of IP Precedence and DSCP Fields
- The three Class Selector bits (DS5 to DS3) broadly classify packets into 8 classes:
- Class 0 – default class, best effort forwarding
- Class 1 through 4 – Assured Forwarding (AF) – higher AF class numbers indicate higher priority traffic. AF traffic can be dropped with the lower class values the most likely to be dropped.
- Class 5 – Expedited Forwarding (EF) – premium service, least likely to be dropped. For time-critical traffic such as voice. DSCP bits cover values from 40-47 but 46 is the only one commonly used with the EF designation.
- Classes 6 and 7 – Internetwork Control and Network Control – usually used for things like STP, and routing protocols.
- Each class has three levels of Drop Precedence contained in bits DS2 through DS0 (DS0 is always zero):
- Low (1)
- Medium (2)
- High (3)
- Within a class, packets with a higher Drop Precedence have more potential for being dropped.
Addendum – Trainsignal Notes
Cisco Switching Fundamentals
- Early LAN protocols – ARCNet, StarLAN, Token Ring
- Ethernet – CSMA/CD, devices listen to the medium (wire) to determine availability
- 10BASE-T – 802.3
- 100BASE-TX – 802.3u
- 1000BASE-TX – 802.3ab
- 10GBASE – 802.3ae
- Port and Interface Types

I do not even know how I ended up here, but I thought this post was great.
I do not know who you are but certainly you are going to a
famous blogger if you aren’t already 😉 Cheers!
awesome notes! Thanks
Very Helpful Notes! Thanks
Thank you for sharing your notes, they are really helpful
thanks a lot. god bless you
Thanks a bunch, really helpful.
can there be a way to have some updated notes even though this onw is helpful
really helped me these notes. keep going.